Android 13 is out and the makers have promised better security enhancements including a special restricted setting feature.
But what if we told you that the promises made have failed to hold through as leading malware developers claim they’ve managed to create droppers to bypass the security feature outlined? Yes, developers say they’ve devised a system based on tactics to overcome the safety features.
The news is alarming and an apparent setback for those with high hopes. Remember, it’s only been a day or two since we last heard about the launch. This was seen across Google’s Pixel phones and AOSP’s source code.
Despite the news, you can’t deny how hard Google tried to disturb mobile malware that made attempts to enter the system using vital and powerful permissions like AccessbilityService.
This way, the malware was allowed to carry out their malicious threats to the systems, making it easy for the company to detect and disable them. But it seems their hard work couldn’t go all the way.
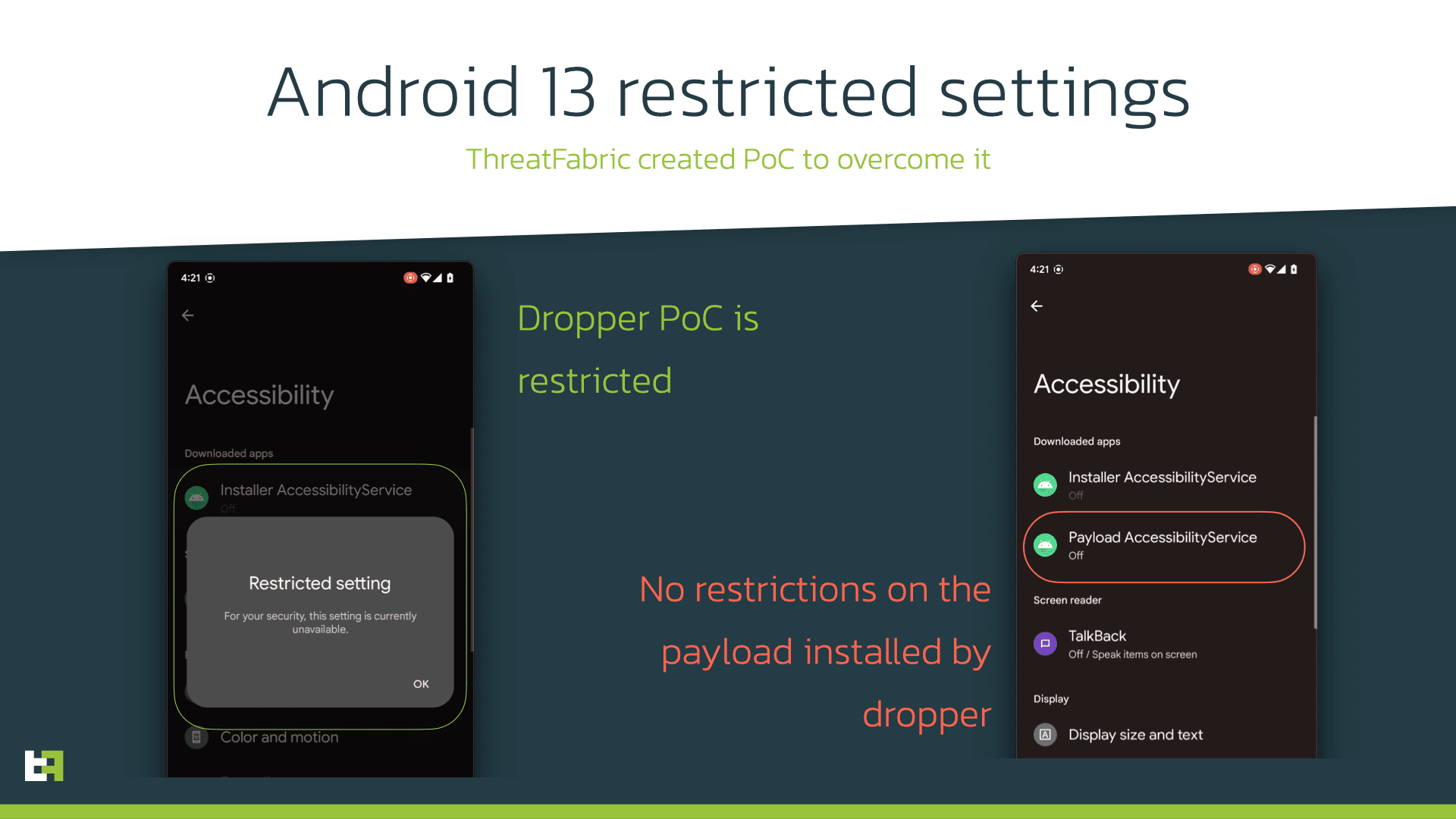
Thanks to a few research experts and tech analysts from Threat Fabric, a new report highlights how malware authors achieved success in creating Android-specific malware droppers that certainly go above and beyond such features.
They end up delivering results that make the most of the users’ devices, leaving them vulnerable to further attack while enjoying the highest privileges.
When we look at Android versions from the past, it’s quite clear how most of them are related to making their way inside the device through apps found simply from Google’s Play Store. They appear legitimate but their true behavior is masqueraded.
At the time of making downloads, different malware apps force users to gain access to various permissions that authors dub risky. On the other end, they’re sideloading dangerous payloads by breaking through the device’s accessibility service.
The latter has been labeled as one of the most easily abused systems out there for Android. With simple touches and swipes, apps are allowed to perform tasks with ease and can even return to home screens with a single tap. And you guessed it, the user has zero clue of what’s really going on.
On usual occasions, the malware has the ability to give itself more permission than allowed. This way, the victim is stopped from making attempts to have the app deleted.
But what really surprises many is how engineers had boasted so much about the new restricted setting functionality. The purpose with which it was designed was to block sideloading from requesting permission from the Accessibility Service. This way, it would be limiting functions to just APKs from Google’s Play Store.
Now, there’s clear proof thanks to Threat Fabric how the system is being fooled easily and bypassed for malicious means into the Accessibility Service.
The malware dropper manages to include some different types of features so it bypasses restricted settings in place.
It’s called BugDrop and while it’s still in its early stage of development, it’s doing a pretty fine job as a novel entity.
The code featured is very similar to that observed with Brox. This is another name provided to malware making its way to different hacking platforms.
With Android 13, search giant Google thought it would be good to restrict entry into the Accessibility Services, other than the Notification Listener to apps getting installed via the session-based method only.
Therefore, if BugDrop was actually using this method for sideloading, it would be detected through the new Android protection system as proven by the malware developers.
For now, BugDrop is in its early creation phase. But soon, it’s going to be ready for further deployment, wreaking havoc across Android devices by the masses.
Read next: New Survey Proves 49% Of Android Users Prefer Switching To iPhones Because It’s Safer
by Dr. Hura Anwar via Digital Information World
No comments:
Post a Comment