People around the globe have relied heavily on the Zoom meetings feature during the pandemic. It is deemed to be the most trusted app while working from home. However, the sources have warned people from downloading the legitimate version of Zoom meetings.
Multiple criminal gangs are making fake versions of the app to download their IP address and steal banking data with other information. The problem could lead you to download nasty viruses and malware into phones and laptops.
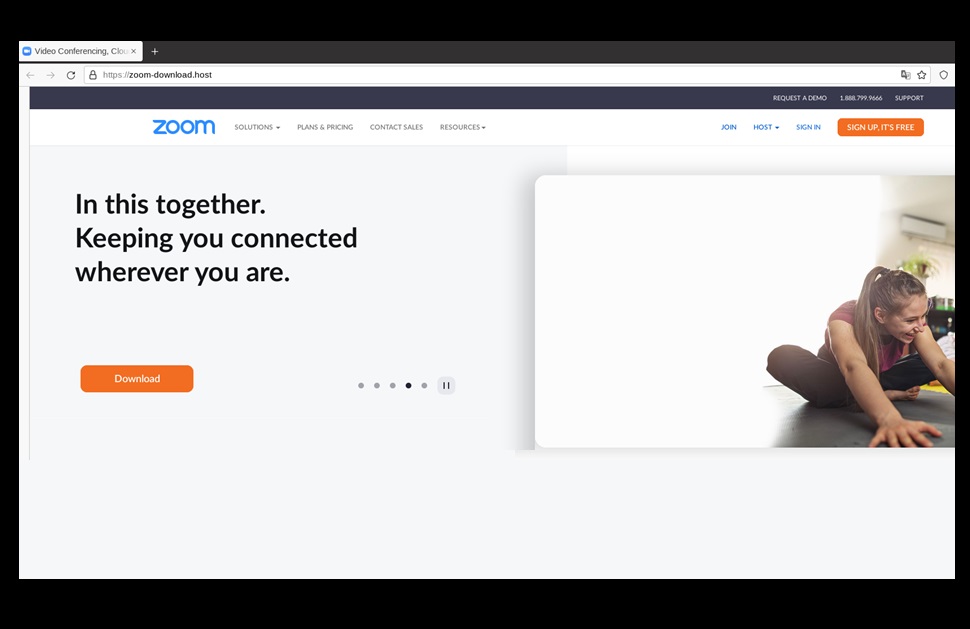
Threat Researchers at Cybersecurity firm Cyble have found six fake zoom sites. These sites have instilled viruses to download all the personal information from your laptops and give access to third-party. The info-stealing virus and other malware variants have been installed to target potential operators of Zoom.
One of the criminal gangs has been unleashed by the Cyble Research and Intelligence Lab (CRIL). Vidar stealer malware can steal banking information, passwords, browser history, IP address, cryptocurrency wallet access, and MFA information. The hacking of the system will later provide the necessary initial access to the stealer.
The researchers have observed that these sites run campaigns to spread information. Furthermore, after gaining access to the private documents of the victim, they sold them to the cybercrime marketplace. The Stealer log has access to breached compromised endpoints.
Whereas, Zoom gained popularity during the pandemic. A wide range of operators has downloaded the app to connect with their colleagues and family members. It has become easier for hackers to prey on broad operators of Zoom. The number of operators has skyrocketed in the past few years.
Zoom reported 204,100 enterprise customers and an 18% increase year by year. The company has also seen a revenue boost, almost reaching $1.1 billion, an 8% jump over the same year. The news has spread all over the world in a short period.
Therefore, the attackers get activated and start targeting the users. The researchers have exposed the six sites uncovered zoom-download[.]host; zoom-download[.]space, zoom-download[.]fun, zoomus[.]host, zoomus[.]tech, and zoomus[.]website. The Register said that they are still operational.
Furthermore, after downloading one of these links, the operator would be redirected to GitHub URL to show options for which application to download. If the user chooses the malicious one, it offers two binaries–ZOOM IN-1. EXE and Decoder. exe—into the temporary folder. The malware also installed itself into MSBuild.exe, which automatically accesses the IP address and fetches configuration data.
Cyble wrote that these threat actors have overlapping Tactics, Techniques, and Procedures with Vidar Stealer. The malware astutely hides the error in the Telegram description. It also hides the IP address of its command and control (C&C) server.
Checking twice where you're obtaining your Zoom programs from is the greatest approach to avoid this infection.
Read next: This New Android Trojan Subscriber Received Nearly 5 Million Downloads
by Arooj Ahmed via Digital Information World
No comments:
Post a Comment