Researchers are ringing alarm bells against a phishing campaign that’s on the rise. It makes use of Facebook posts that becomes a part of the attack chain for tricking users. The campaign secretly makes users hand over sensitive details like account credentials and other personal information.
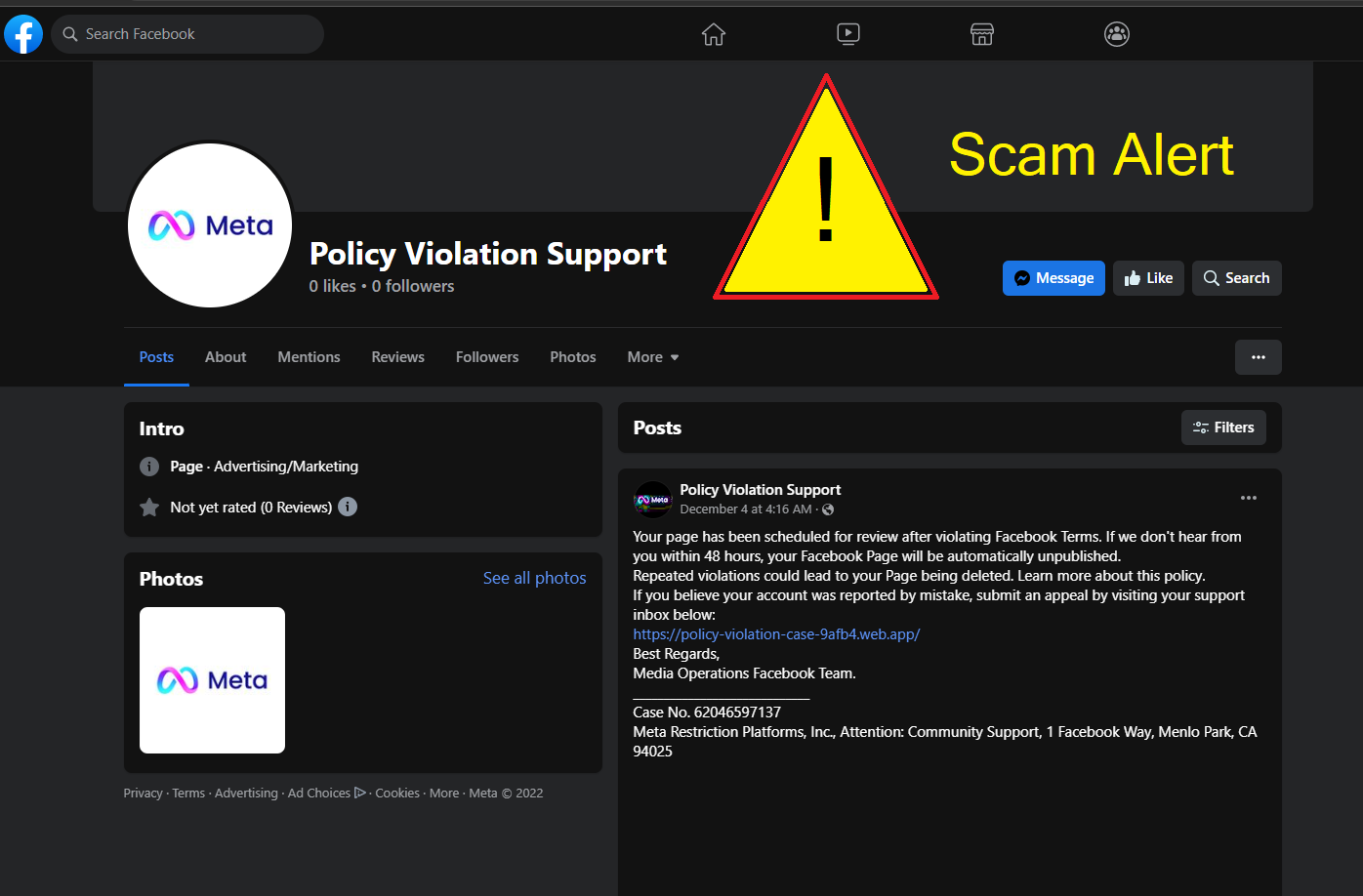
These emails are sent out to different targets and they pretend as if it’s copyright infringement matters on a particular recipient’s post on Facebook. They send out warnings about accounts getting deleted if the two-day time limit is crossed and no response is generated such as an appeal getting filed.
Many users have become victims of this scam because it does look so real. The links provided for appeals of the account deletion arise in the form of a real post from the Facebook app. This enables the malicious threat actors to bypass security enlisted for email solutions. Moreover, it ensures that phishing messages end up in the users’ target inbox.
The post on Facebook acts like it’s a Page Support and even uses logos from Facebook to make it appear as if the network manages it. But the post actually entails links for external phishing websites that are named after the likes of Meta which is Facebook’s parent firm. The whole idea is to make the scam campaign appear as real as possible so victims don’t realize the truth soon.
The news comes to us thanks to analysts at Trustwave. They were the first ones to highlight the campaign by following some URLs that are up on Facebook.
Each phishing website is carefully curated with immense care to have it appear as it is on Facebook’s real appeal page. There’s even a form where you can find victims requesting full names, email IDs, addresses, contact numbers, and usernames across Facebook.
After such data is submitted by a victim, the page manages to steal the IP address and location details. These are transferred to a new account on the Telegram app that’s under their complete control.
In some cases, you can see the threat actors collecting data like extra personal information that could bypass the likes of fingerprinting protection or any other added security measure while conducting a complete takeover.
And there are cases where a redirection would forward the victim to another similar phishing page that entails fake OTP password requests that are time-sensitive.
After adding the code, users would notice how an error sign arrives. Similarly, the experts have highlighted how the actors are resorting to Google Analytics across phishing pages to assist with tracking efficiency.
This happens to be a widespread technique that so many actors are using and TrustWave claims it has managed to locate several accounts on the Facebook app that use such phony posts. It appears in the form of support pages that push victims toward phishing sites.
During our separate research we found even more freshly created Facebook pages and posts, we reported them to Facebook, but unfortunately we don't have the bandwidth to report them all. But Facebook must have moderation tools and teams in place to curb this issue.
Sadly, Facebook and Meta, after being repeatedly informed about this matter, failed to come up with a strategy to proactively deal with bad actors on its platform. Phishing actors keep on improving their tactics to hack Facebook users but it appears the social media giant has not learned its lesson yet.
Being aware and steering clear is definitely the way to go here and save yourself from turning into a victim, experts claim.
Read next: These Countries Are the Most Dangerous for Journalists
by Dr. Hura Anwar via Digital Information World

No comments:
Post a Comment